Cyber Security in BPO Industry
With outsourcing industries growing bigger than ever before, a lot of organizations have effectively reduced costs, improved their operational efficiency, and managed their core activities timely. From content and cataloging to revenue enhancement, there isn’t any non-core activity that does not have a competitive outsourcing provider available in the market.
Data security is one of the major challenges that companies face due to ineffective third-party controls and IT security threats. With new technologies, such as artificial intelligence, machine learning, and robotic process automation, the need for strict data security is at an all-time high. Therefore, stringent data security policies are usually questioned when a firm chooses its outsourcing provider.
Transform your outsourcing with the best BPO provider
Cyber Security: The Most Important Challenge for the BPO Industry
Security is a critical challenge that needs to be taken care of while outsourcing your activities to any service provider.
Technological Evolution
As technologies evolve, so do the intricacies of data security. Global networks and digitalization have increased the level of threats possible in the industry.
“30% of the security experts deal with fishing attacks every day.” – State of Cybersecurity Survey, ISACA
Monetary gains, secret information leakages, spear phishing, disguised emails, social media, work accounts, and employee card information can be identified easily by hackers. Digital data is vulnerable to security breaches, with valuable information at risk of being accessible to a lot of individuals through a shared network.
Many BPO security threats, such as phishing, hacking, malware, and other malicious techniques, have improved over time and should be handled properly.
Innovations
Businesses are paving their way towards cloud businesses, digital transformation, and Internet of Things (IoT) security. Most entrepreneurs are concerned about protection against governance, risk management, threat management, authentication, and data privacy in BPO and professional security services.
Remote Work
Attackers seek to leverage security gaps while telecommuting using insecure devices and networks. To maintain momentum and support business continuity, it is imperative that the core dimensions of your business should not be impacted. All the risks associated with digital work environment – supply chain, channel partners, customers – should follow specific, industry-wise security measures.
Cyber security teams are now perceived anew and should be recognized as an important asset for taking strategic decisions.
Possible threats due to online data leakages include:
- Fraudulent transactions
- Exposure of data
- Unreliable resources posing security threats
- Permissible remote devices for omnichannel support
- Unauthorized access to sensitive data
Cyber Security Education
Employees have started to expand their technology horizons and need to be educated as technology further evolves. It is important for you to give your employees proper training on which devices to use, VPN, Firefox, and using shared network information. Botnets are another data threat to security and may harness information, such as name, address, age, financial information, gender, online activity, etc. This makes personal information vulnerable for anyone. With increased information on technology, it is important that your employees are trained more than hackers.
Social Media Security
Social media hackers can access not just your personal information but a few applications can also access a consumer’s location data. On social media platforms, a lot of people can check your location, your moods, your likes and dislikes, and your idle time status. Such indicators can directly put your valuable information and safety at risk. Every device serves as another asset for a cyber security attacker and can result in several malware issues emerging from the system.
Non-timely System Upgrades
When systems are not updated for a long duration, there is a higher probability that they will get corrupted. When we download a new file from the system, there may be a chance that it may get stored in the local storage and attack the system if it is not safe to use. Data breaches and system vulnerabilities are quite common during such non-timely system upgrades.
It is, therefore, extremely, important for BPO enterprises to follow secure coding practices to not compromise on their reputation in case of any unforeseen circumstances. Also, once the policies are in place, implementation becomes another necessity to make all stakeholders adhere to the specified rules.
Common practices include –
- Restricting multiple devices and cellphones, especially on the production floor
- Authorizing access to specific users only to access important areas
- Checks at entry and exit gates
- Timely regulatory training to employees
Regulatory Changes and Stricter Compliance Norms are the Way Forward
Recently, rules regarding cyber security in India were updated with a strong emphasis on robust policies for citizens and businesses. Timely actions to combat cyber threats were announced by the government in 2020 and the updated guidelines are awaited for 2021. A strong framework with stringent policies will provide the way forward to handle cybercrime issues.
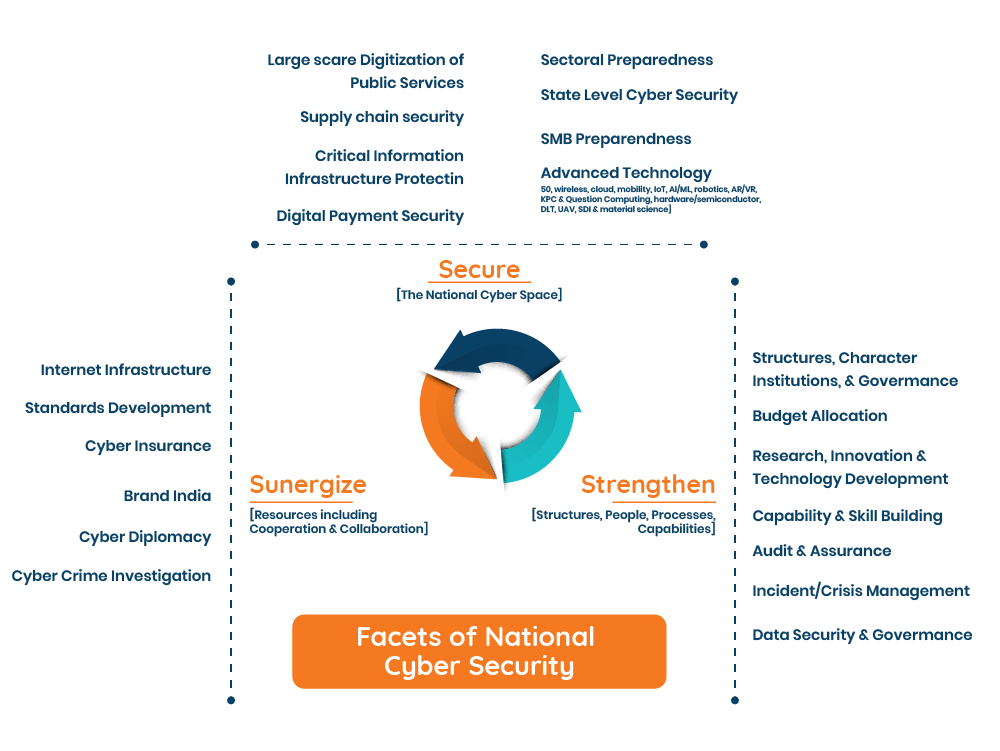
Source: National Cyber Security
The following are some of the initiatives by the Indian government:
- Indian Cyber Crime Coordination Centre (I4C)
- National Critical Information Infrastructure Protection Centre (NCIIPC)
- Information Technology Act, 2000
- National Cyber Policy, 2013
- Cyber Surakshit Bharat Initiative
- Cyber Swachhta Kendra
- Online Cybercrime Reporting Portal
India is the 17th largest digital economies globally and is a key player in digitalizing its operational processes. (Source: Indian Express)
Even in the name of covid-crisis vaccines, fraudsters have started calling people to gain access to their personal information and bank details. In such a vulnerable space, prevention of all fraudulent activities is not possible.
To address these gaps, the government must go for a layered security system wherein security threat intelligence should operate between various layers. Operational strategic alliances between agencies and coordinators will prove to be a successful move to dissuade cyber attackers. Furthermore, proper monitoring of IT infrastructure and compliance along with awareness programs would manage these risks effectively.










